Difference between revisions of "NoAuth usecase 1"
Pavel.lobko (talk | contribs) |
Pavel.lobko (talk | contribs) |
||
| Line 2: | Line 2: | ||
| − | With *None Authentication method chosen, all you have to do - specify URI to be requested and request type. <br> | + | With <code>*None</code> [[Authentication method]] chosen, all you have to do - specify URI to be requested and request type. <br> |
[[File:Noauth-1.png]] | [[File:Noauth-1.png]] | ||
I2REST COMMAND(*GET) URL('http://apache.org') AUTHMETHOD(*NONE) | I2REST COMMAND(*GET) URL('http://apache.org') AUTHMETHOD(*NONE) | ||
Revision as of 13:43, 2 April 2020
Http/Https request without authorization
With *None Authentication method chosen, all you have to do - specify URI to be requested and request type.
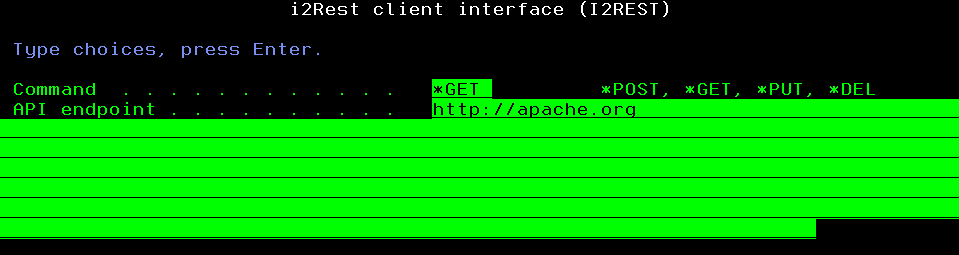
I2REST COMMAND(*GET) URL('http://apache.org') AUTHMETHOD(*NONE)
Lets exemine some more complicated example:
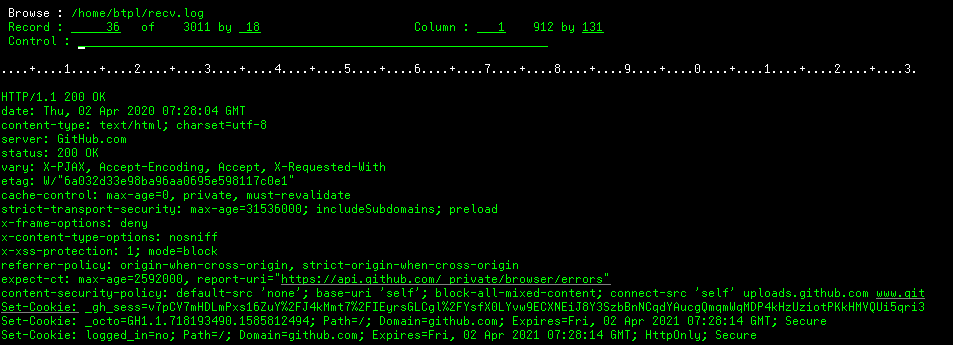
I2REST COMMAND(*GET) URL('https://github.com') OUTPUT(*BOTH)
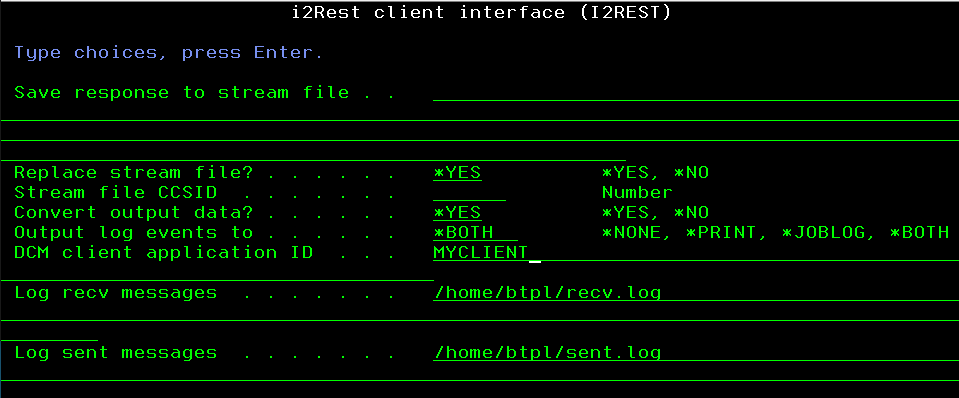
DCMCLIENT(MYCLIENT) RECVLOG('/home/btpl/recv.log') SENTLOG('/home/btpl/sent.log')
AUTHMETHOD(*NONE)
Dealing with ssl/tls secured resources you have to setup your IBM i DCM client.
Result of a request could be checked in a joblog and/or printer output file, according to a value of « Output log events to» parameter.
All the data transferred from/to remote server will be saved to log files specified in parameters « Log recv messages” and “Log sent messages».