Difference between revisions of "Device flow description"
Pavel.lobko (talk | contribs) |
Pavel.lobko (talk | contribs) |
||
| (48 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | {{DISPLAYTITLE:Device | + | {{DISPLAYTITLE:Device flow description}} |
| + | ==Overview== | ||
| + | [https://tools.ietf.org/html/rfc8628 Oauth 2.0 Device flow] is the authorization scenario for those devices (like IBM i), that has no ability to display an authorization web page when making request to private data on resources with limited access. <br> | ||
| + | [[File:Device-flow-scheme1.png|400px]] | ||
| + | <br> | ||
| + | Device flow scheme. | ||
| + | (A) i2Rest Client initiates the flow with a request to the authorization server. The request incudes client identifier and requested scope.<br> | ||
| + | (B) The authorization server responds with a device code, an end-user code and the verification URL.<br> | ||
| + | (C) i2Rest Client displays an end-user code and the verification URL and thus instructs the end user to visit authorization page using a user agent on another device.<br> | ||
| + | (D) The end-user follows provided verification URL on any browser capable device. The authorization server authenticates the resource owner and performs authorization dialog to determin either access will be granted or denied.<br> | ||
| + | (E) i2Rest Client starts polling authorization server with device code to determine whether the user has authorized the request.<br> | ||
| + | (F) The authorization server authenticates the client, performs validation of the device code, and, if access was granted by end user, responds with an access token.<br> | ||
| + | ==Device flow by i2Rest command== | ||
| + | The next parameters are mandatory to perform request with Device flow by I2Rest command.<br> | ||
| − | + | {| class="wikitable" | |
| − | + | ! Keyword !! Parameter!! Description | |
| − | + | |- | |
| − | + | |[[I2Rest_Client_command#AUTHMETHOD | AUTHMETHOD]] || Authentication method ||*OAUTH2D must be specified | |
| − | + | |- | |
| − | + | |[[I2Rest_Client_command#COMAND| COMAND ]] || Request type || Any of available request type can be choosen | |
| − | + | |- | |
| − | + | |[[I2Rest_Client_command#URL| URL ]] || API endpoint || HTTP resource to serve the request | |
| − | + | |- | |
| − | + | |[[I2Rest_Client_command#AUTHID| AUTHID]] || User/OAuth2 client/device ID ||rowspan="2"| Credentials to authenticate I2Rest Client with authorization server | |
| − | + | |- | |
| − | + | |[[I2Rest_Client_command#AUTHPW| AUTHPW]] || User/OAuth2 client/dev passwd | |
| − | + | |- | |
| − | + | |[[I2Rest_Client_command#AUTHURL| AUTHURL ]] ||OAuth2 authorization endpoint || HTTP resource to be requested for an authorization URL and device code | |
| − | + | |- | |
| − | + | |[[I2Rest_Client_command#TOKENURL| TOKENURL]] ||Token endpoint ||HTTP resource to be requested for an access token | |
| − | + | |- | |
| − | + | |[[I2Rest_Client_command#SCOPE| SCOPE]] || Scope || The set of resources and operations that are allowed to application with access token | |
| − | + | |- | |
| − | + | |} | |
| − | + | i2Rest command example bellow represents request for creating i2rest.doc file on Google Drive, please explore [[Device_flow_usecase_1|the appropriate use case]]. | |
| − | + | <pre> | |
| − | + | I2REST COMMAND(*POST) | |
| − | + | URL('https://www.googleapis.com/drive/v3/files') | |
| − | + | BODY(*N '{"name":"i2rest.doc"}' | |
| − | + | 'application/json' *YES 1208) | |
| − | + | OUTPUT(*BOTH) | |
| − | + | AUTHMETHOD(*OAUTH2D) | |
| − | + | DCMCLIENT(MYCLIENT) | |
| − | + | TOKENS('/tokens/tokens.usrspc') | |
| − | + | AUTHID('<client ID>') | |
| − | + | AUTHPW('<client secret>') | |
| − | + | AUTHURL('https://oauth2.googleapis.com/device/code') | |
| − | + | TOKENURL('https://oauth2.googleapis.com/token') | |
| − | + | SCOPE('https://www.googleapis.com/auth/drive.file') | |
| − | + | </pre> | |
Latest revision as of 13:04, 9 September 2020
Overview
Oauth 2.0 Device flow is the authorization scenario for those devices (like IBM i), that has no ability to display an authorization web page when making request to private data on resources with limited access.
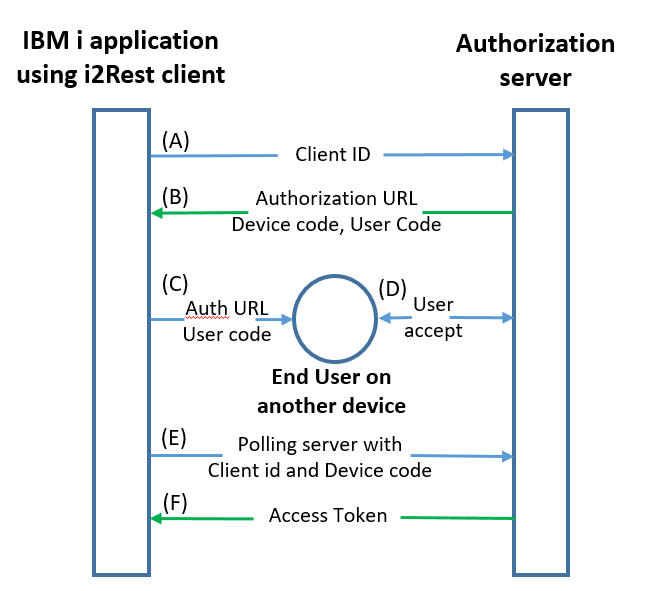
Device flow scheme.
(A) i2Rest Client initiates the flow with a request to the authorization server. The request incudes client identifier and requested scope.
(B) The authorization server responds with a device code, an end-user code and the verification URL.
(C) i2Rest Client displays an end-user code and the verification URL and thus instructs the end user to visit authorization page using a user agent on another device.
(D) The end-user follows provided verification URL on any browser capable device. The authorization server authenticates the resource owner and performs authorization dialog to determin either access will be granted or denied.
(E) i2Rest Client starts polling authorization server with device code to determine whether the user has authorized the request.
(F) The authorization server authenticates the client, performs validation of the device code, and, if access was granted by end user, responds with an access token.
Device flow by i2Rest command
The next parameters are mandatory to perform request with Device flow by I2Rest command.
| Keyword | Parameter | Description |
|---|---|---|
| AUTHMETHOD | Authentication method | *OAUTH2D must be specified |
| COMAND | Request type | Any of available request type can be choosen |
| URL | API endpoint | HTTP resource to serve the request |
| AUTHID | User/OAuth2 client/device ID | Credentials to authenticate I2Rest Client with authorization server |
| AUTHPW | User/OAuth2 client/dev passwd | |
| AUTHURL | OAuth2 authorization endpoint | HTTP resource to be requested for an authorization URL and device code |
| TOKENURL | Token endpoint | HTTP resource to be requested for an access token |
| SCOPE | Scope | The set of resources and operations that are allowed to application with access token |
i2Rest command example bellow represents request for creating i2rest.doc file on Google Drive, please explore the appropriate use case.
I2REST COMMAND(*POST)
URL('https://www.googleapis.com/drive/v3/files')
BODY(*N '{"name":"i2rest.doc"}'
'application/json' *YES 1208)
OUTPUT(*BOTH)
AUTHMETHOD(*OAUTH2D)
DCMCLIENT(MYCLIENT)
TOKENS('/tokens/tokens.usrspc')
AUTHID('<client ID>')
AUTHPW('<client secret>')
AUTHURL('https://oauth2.googleapis.com/device/code')
TOKENURL('https://oauth2.googleapis.com/token')
SCOPE('https://www.googleapis.com/auth/drive.file')