Difference between revisions of "Authorization Code flow description"
Pavel.lobko (talk | contribs) |
m |
||
| (41 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | {{DISPLAYTITLE: | + | {{DISPLAYTITLE:Authorization Code flow using i2Rest bridge mode}} |
| − | + | ==Overview== | |
| − | + | Authorization Code flow using i2Rest bridge has not too much diferencies from [https://tools.ietf.org/html/rfc6749#section-4.1 original Authorization Code flow] - we just have to implement two "bridges" to solve IBM i functional limitations. Here are limitations and our solutions: | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | The | + | * i2Rest Client is not capable of interacting with the resource owner's user-agent (typically a web browser), this functions are delegated to the i2Rest Server. To perform the delegation i2Rest Client have to provide i2Rest Server with all the necessery request details and bring the end user's agent to i2Rest Server Bridge endpoint. This process is described in steps A-B-C on the scheme bellow.<br> |
| + | * i2Rest Client also is not capable of receiving incoming requests via redirection, so I2Rest Server have to receive Authorization Server redirection with access code attached. Then obtained access code should be linked to initial I2Rest Client to Server communication, and returned to the Client uppon request. The process is described in steps G-E-H on the scheme bellow.<br> | ||
| − | + | [[File:Bridge flow scheme.png|700px]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Bridge flow scheme.<br> | |
| − | |||
| − | |||
| − | + | (А) i2Rest Client initiates the flow with a request to the I2Rest Server Bridge endpoint. The request incudes client identifier, requested scope and Authorization Server URL (authorization endpoint). | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | (B) I2Rest Server responds with Brigde URL, Bridge User Code and Bridge Code. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | (C) i2Rest Client instructs the user to visit provided Brigde URL using device with input capability and browser support. | |
| − | + | ||
| − | + | (D) i2Rest Server directs the resource owner's user-agent to the authorization endpoint. Request contains i2Rest Client identifier, requested scope, Bridge local state, redirection Bridge URI to which the authorization server will send the user-agent back once access is granted (or denied). | |
| − | + | ||
| − | + | (E) i2Rest Client starts polling I2Rest Server bridge with Bridge code to determine whether the user has authorized the request. | |
| − | -- | + | |
| − | [[ | + | (F) The authorization server authenticates the resource owner and performs authorization dialog to determin either access will be granted or denied. |
| + | |||
| + | (G) The authorization server redirects the user-agent to the i2Rest Server bridge using the redirection URI provided earlier in the request or during client registration. The redirection URI includes an authorization code. Bridge local state will be checked for matching the one included in the request on step D for preventing cross-site request forgery. | ||
| + | |||
| + | (H) i2Rest Server bridge responds to Client polling request with authorization code if access was granted or with an error if access was denied. | ||
| + | |||
| + | (I) i2Rest Client requests authorization server's token endpoint with the authorization code and exchanges it for an access token. Request includes i2Rest Client credentials for authentication with the authorization server and redirection URI used to obtain the authorization code for verification. | ||
| + | |||
| + | (J) The authorization server authenticates the client, performs validation of the authorization code and the redirection URI, and, If valid, responds with an access token. | ||
| + | |||
| + | ==Authorization Code flow by i2Rest command== | ||
| + | The next parameters are mandotary to perform request with Authorization code flow by I2Rest command.<br> | ||
| + | {| class="wikitable" | ||
| + | ! Keyword !! Parameter!! Description | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#AUTHMETHOD | AUTHMETHOD]] || Authentication method || *BRIDGE must be specified | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#COMAND| COMAND ]] || Request type || Any of available request type can be choosen | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#URL| URL ]] || API endpoint || HTTP resource to serve the request | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#AUTHID| AUTHID]] || User/OAuth2 client/device ID ||rowspan="2"| Credentials to authenticate I2Rest Client with authorization server | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#AUTHPW| AUTHPW]] || User/OAuth2 client/dev passwd | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#AUTHURL| AUTHURL ]] ||OAuth2 authorization endpoint || HTTP resource to be requested for an authorization code | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#TOKENURL| TOKENURL]] ||Token endpoint ||HTTP resource to be requested for an access token | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#SCOPE| SCOPE]] || Scope || The set of resources and operations that are allowed to application with access token | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#BRIDGEURL| BRIDGEURL]] || i2Rest access flow bridge url ||Redirection URI to be passed to authorization server | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#BRIDGEID| BRIDGEID]]|| i2Rest bridge client ID ||rowspan="2"| Credentials to authenticate I2Rest Client with i2rest Server | ||
| + | |- | ||
| + | |[[I2Rest_Client_command#BRIDGEPW| BRIDGEPW ]] ||i2Rest bridge client password | ||
| + | |- | ||
| + | |} | ||
| + | i2Rest command example bellow represent request for Google Drive file list: | ||
| + | <pre> | ||
| + | I2REST COMMAND(*GET) | ||
| + | URL('https://www.googleapis.com/drive/v3/files') | ||
| + | OUTPUT(*BOTH) | ||
| + | DCMCLIENT(MYCLIENT) | ||
| + | AUTHMETHOD(*BRIDGE) | ||
| + | TOKENS('/qsys.lib/qtemp.lib/tokens.usrspc') | ||
| + | AUTHID('Device ID') | ||
| + | AUTHPW('Device password') | ||
| + | AUTHURL('https://accounts.google.com/o/oauth2/v2/auth | ||
| + | ') | ||
| + | TOKENURL('https://oauth2.googleapis.com/token') | ||
| + | SCOPE('https://www.googleapis.com/auth/drive.file') | ||
| + | BRIDGEURL('<Bridge endpoint>') | ||
| + | BRIDGEID('<Client name>') | ||
| + | BRIDGEPW('<Client password>') | ||
| + | </pre> | ||
| + | |||
| + | This use case is described in detail in our [[Authorization_code_usecase_1|use case book]]. | ||
Latest revision as of 12:19, 7 September 2020
Overview
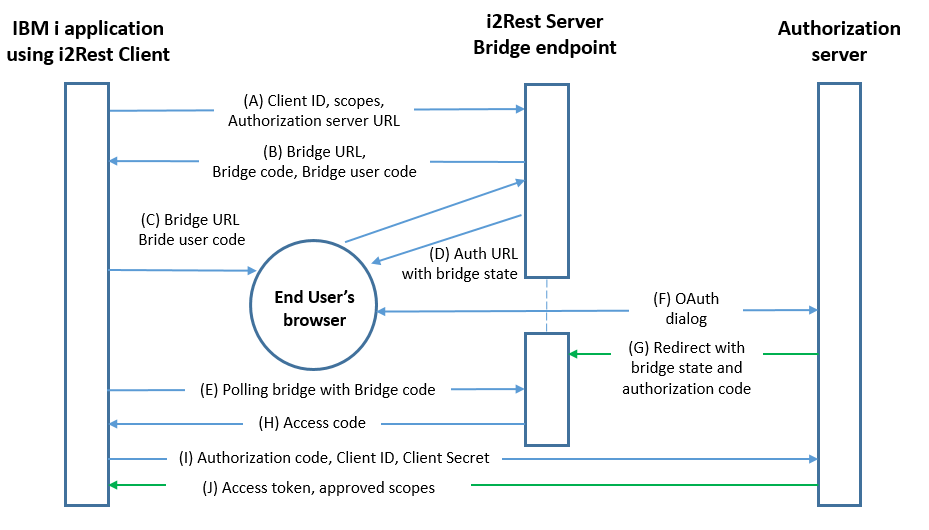
Authorization Code flow using i2Rest bridge has not too much diferencies from original Authorization Code flow - we just have to implement two "bridges" to solve IBM i functional limitations. Here are limitations and our solutions:
- i2Rest Client is not capable of interacting with the resource owner's user-agent (typically a web browser), this functions are delegated to the i2Rest Server. To perform the delegation i2Rest Client have to provide i2Rest Server with all the necessery request details and bring the end user's agent to i2Rest Server Bridge endpoint. This process is described in steps A-B-C on the scheme bellow.
- i2Rest Client also is not capable of receiving incoming requests via redirection, so I2Rest Server have to receive Authorization Server redirection with access code attached. Then obtained access code should be linked to initial I2Rest Client to Server communication, and returned to the Client uppon request. The process is described in steps G-E-H on the scheme bellow.
Bridge flow scheme.
(А) i2Rest Client initiates the flow with a request to the I2Rest Server Bridge endpoint. The request incudes client identifier, requested scope and Authorization Server URL (authorization endpoint).
(B) I2Rest Server responds with Brigde URL, Bridge User Code and Bridge Code.
(C) i2Rest Client instructs the user to visit provided Brigde URL using device with input capability and browser support.
(D) i2Rest Server directs the resource owner's user-agent to the authorization endpoint. Request contains i2Rest Client identifier, requested scope, Bridge local state, redirection Bridge URI to which the authorization server will send the user-agent back once access is granted (or denied).
(E) i2Rest Client starts polling I2Rest Server bridge with Bridge code to determine whether the user has authorized the request.
(F) The authorization server authenticates the resource owner and performs authorization dialog to determin either access will be granted or denied.
(G) The authorization server redirects the user-agent to the i2Rest Server bridge using the redirection URI provided earlier in the request or during client registration. The redirection URI includes an authorization code. Bridge local state will be checked for matching the one included in the request on step D for preventing cross-site request forgery.
(H) i2Rest Server bridge responds to Client polling request with authorization code if access was granted or with an error if access was denied.
(I) i2Rest Client requests authorization server's token endpoint with the authorization code and exchanges it for an access token. Request includes i2Rest Client credentials for authentication with the authorization server and redirection URI used to obtain the authorization code for verification.
(J) The authorization server authenticates the client, performs validation of the authorization code and the redirection URI, and, If valid, responds with an access token.
Authorization Code flow by i2Rest command
The next parameters are mandotary to perform request with Authorization code flow by I2Rest command.
| Keyword | Parameter | Description |
|---|---|---|
| AUTHMETHOD | Authentication method | *BRIDGE must be specified |
| COMAND | Request type | Any of available request type can be choosen |
| URL | API endpoint | HTTP resource to serve the request |
| AUTHID | User/OAuth2 client/device ID | Credentials to authenticate I2Rest Client with authorization server |
| AUTHPW | User/OAuth2 client/dev passwd | |
| AUTHURL | OAuth2 authorization endpoint | HTTP resource to be requested for an authorization code |
| TOKENURL | Token endpoint | HTTP resource to be requested for an access token |
| SCOPE | Scope | The set of resources and operations that are allowed to application with access token |
| BRIDGEURL | i2Rest access flow bridge url | Redirection URI to be passed to authorization server |
| BRIDGEID | i2Rest bridge client ID | Credentials to authenticate I2Rest Client with i2rest Server |
| BRIDGEPW | i2Rest bridge client password |
i2Rest command example bellow represent request for Google Drive file list:
I2REST COMMAND(*GET)
URL('https://www.googleapis.com/drive/v3/files')
OUTPUT(*BOTH)
DCMCLIENT(MYCLIENT)
AUTHMETHOD(*BRIDGE)
TOKENS('/qsys.lib/qtemp.lib/tokens.usrspc')
AUTHID('Device ID')
AUTHPW('Device password')
AUTHURL('https://accounts.google.com/o/oauth2/v2/auth
')
TOKENURL('https://oauth2.googleapis.com/token')
SCOPE('https://www.googleapis.com/auth/drive.file')
BRIDGEURL('<Bridge endpoint>')
BRIDGEID('<Client name>')
BRIDGEPW('<Client password>')
This use case is described in detail in our use case book.