Difference between revisions of "Device flow description"
Pavel.lobko (talk | contribs) |
Pavel.lobko (talk | contribs) |
||
| Line 1: | Line 1: | ||
{{DISPLAYTITLE:Device Flow Description}} | {{DISPLAYTITLE:Device Flow Description}} | ||
| − | [[File:Device-flow- | + | [[File:Device-flow-scheme.png]] |
<br> | <br> | ||
Revision as of 14:59, 7 April 2020
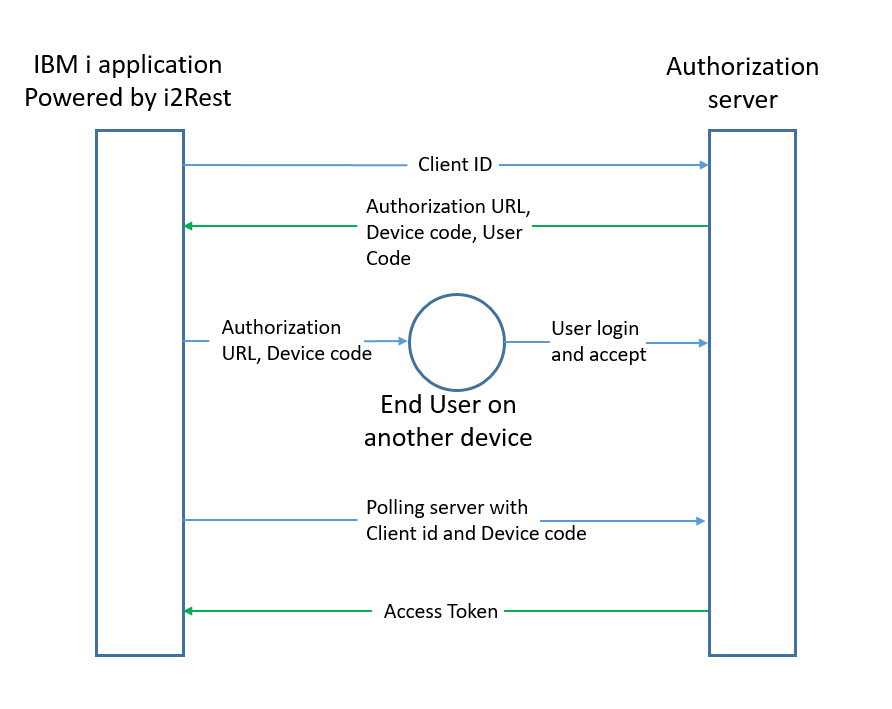
The flow consists of the following steps:
(A) The client requests access from the authorization server and
includes its client identifier in the request.
Your application sends a request to auth serv OAuth2 authorization endpoint that identifies the scopes that your application will request permission to access.
With obtained on client registration
(B) The authorization server issues a device code and an end-user
code and provides the end-user verification URI.
The authorization server responds with a device code, end-user code and verification URI, to be shown to end-user.
(C) The client instructs the end user to visit the provided end-user verification URI on any capabable device. The
client provides the user with the end-user code to enter in
order to review the authorization request. .
(D) The authorization server authenticates the end user (via the
user agent), and prompts the user to input the user code
provided by the device client. The authorization server
validates the user code provided by the user, and prompts the
user to accept or decline the request.
The user switches to a device with richer input capabilities, launches a web browser, navigates to the URL displayed in step 3 and enters a code that is also displayed in step 3. The user can then grant (or deny) access to your application.
(E) While the end user reviews the client's request (step D), the
client repeatedly polls the authorization server to find out if
the user completed the user authorization step. The client
includes the device code and its client identifier. Your application starts polling Google's authorization server to determine whether the user has authorized your app.
(F) The authorization server validates the device code provided by
the client and responds with the access token if the client is
granted access, an error if they are denied access, or an
indication that the client should continue to poll.