Difference between revisions of "Device flow description"
Pavel.lobko (talk | contribs) |
Pavel.lobko (talk | contribs) m (Pavel.lobko moved page Device-flow-decription to Device-flow-description) |
(No difference)
| |
Revision as of 16:03, 7 April 2020
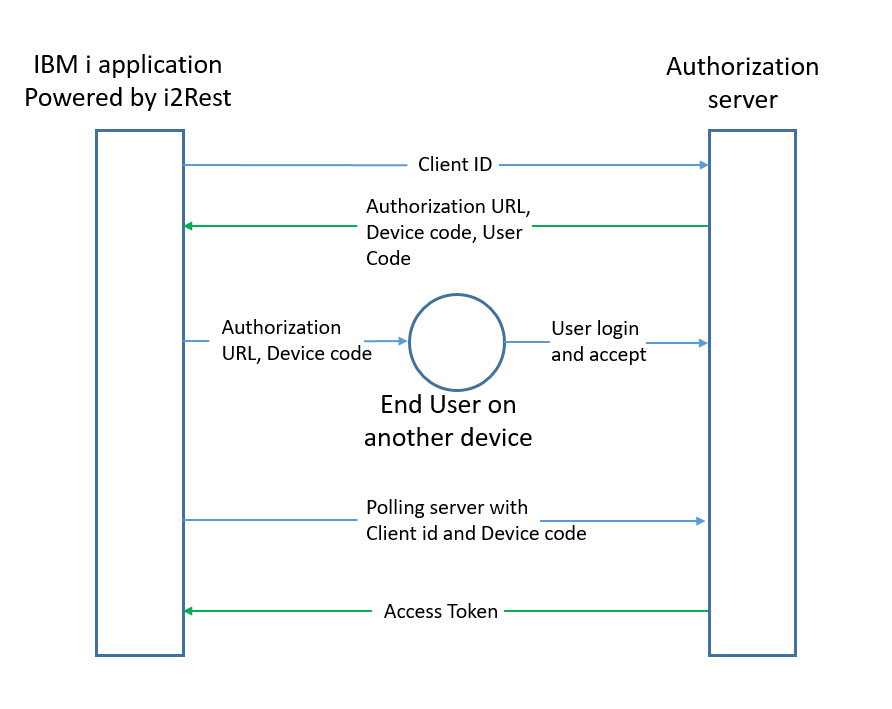
The flow consists of the following steps:
- i2Rest client sends a request to the authorization server and includes its client identifier in the request.
- The authorization server responds with a device code, an end-user code and the verification URL.
- i2rest client provides end-user with a device code and the verification URL.
- Now it's time end-user to follow provided verification URL on any capable device. After authentification on authorization server end-user will be prompted to grant (or deny) access to the application.
- At the time end-user i2 rest starts polling authorization server.
- The authorization server validates the device code provided by the client and responds with the access token if the client is granted access, an error if they are denied access, or an indication that the client should continue to poll.