Difference between revisions of "Noauth description"
Pavel.lobko (talk | contribs) |
Pavel.lobko (talk | contribs) |
||
| Line 1: | Line 1: | ||
{{DISPLAYTITLE:Https request without authentication}} | {{DISPLAYTITLE:Https request without authentication}} | ||
| − | Saying "request without | + | Saying "request without authentication" we mean that no authentication data is handling by default with this option. When you use one of the other three options, i2Rest client will do some magic to make your request authenticated, but with this one - everything in your hands. So [[Client_flow_description|Client credential flow]] and [[Device_flow_description|here]] |
== The simpliest example == | == The simpliest example == | ||
| Line 17: | Line 17: | ||
Result of a request could be checked in a joblog and/or printer output file, according to a value of «Output log events to» parameter.<br> | Result of a request could be checked in a joblog and/or printer output file, according to a value of «Output log events to» parameter.<br> | ||
All the data transferred from/to remote server will be saved to log files specified in parameters «Log recv messages» and «Log sent messages».<br> | All the data transferred from/to remote server will be saved to log files specified in parameters «Log recv messages» and «Log sent messages».<br> | ||
| − | |||
| − | |||
Revision as of 13:38, 30 April 2020
Saying "request without authentication" we mean that no authentication data is handling by default with this option. When you use one of the other three options, i2Rest client will do some magic to make your request authenticated, but with this one - everything in your hands. So Client credential flow and here
The simpliest example
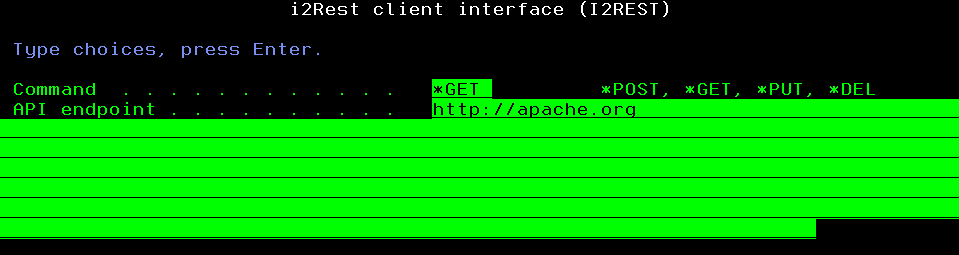
Just choose *None Authentication method, specify URI to be requested and request type - that's all.
I2REST COMMAND(*GET) URL('http://apache.org') AUTHMETHOD(*NONE)
Handling logs and SSL
Lets exemine some more complicated example:
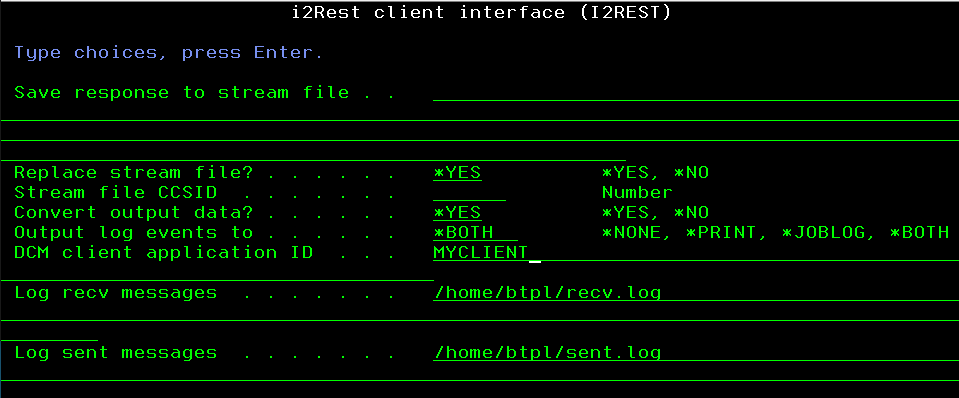
I2REST COMMAND(*GET) URL('https://github.com') OUTPUT(*BOTH)
DCMCLIENT(MYCLIENT) RECVLOG('/home/btpl/recv.log') SENTLOG('/home/btpl/sent.log')
AUTHMETHOD(*NONE)
Dealing with SSL/TLS secured resources you have to setup your IBM i DCM client.
Result of a request could be checked in a joblog and/or printer output file, according to a value of «Output log events to» parameter.
All the data transferred from/to remote server will be saved to log files specified in parameters «Log recv messages» and «Log sent messages».