Difference between revisions of "I2Rest Client"
Pavel.lobko (talk | contribs) |
(→Implementation) |
||
| (36 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
{{DISPLAYTITLE:i2Rest Client}} | {{DISPLAYTITLE:i2Rest Client}} | ||
| + | i2Rest Client is a native IBM i tool for web communications via http/https requests. It was intended to extend IBM i interactive green screen and batch functionality with http client functions. i2Rest Client takes on all the difficulties associated with interaction between your programs and all the outside world - from providing transport functions to implementing various authentication and authorization scenarios (like OAuth2.0 flows), which allows your IBM i to have access to almost any web service. | ||
| − | + | [[File:I2Rest Client flow.png]] | |
| − | |||
| − | == | + | == Request authorization methods == |
| − | <div id="scenaries"></div>Depending on your | + | <div id="scenaries"></div>Depending on your target server requirements, you can choose one of the next request authorization metods provided by i2Rest Client: |
| − | |||
| − | |||
| − | : | ||
| + | ;Request without authorization | ||
| + | :HTTP/HTTPS requests of any type, JSON messages, stream file upload - everything is [[Noauth_description|here]]. Please explore [[i2Rest_Client_Usecases#https_request_without_authorization|typical use cases]] | ||
;Basic access authentication | ;Basic access authentication | ||
| − | :Same options as above, but with [ | + | :Same options as above, but with [https://en.wikipedia.org/wiki/Basic_access_authentication Basic access authentication]. |
| + | <br> | ||
| + | The next three methods are the [https://oauth.net/2/ OAuth2.0] flows, which are the way of enabling third party application to have limited access to protected user data on remote resource behalf of a data owner. The benefit of OAuth2.0 flows is that data owners are not forced to share their usernames, passwords, and other private information to third party applictaions. | ||
;OAuth2 Client Credentials flow | ;OAuth2 Client Credentials flow | ||
| − | : | + | :Client Credentials flow should be used to authenticate your IBM i application on remote resource to work with its own data rather than a user's data. [[Client_flow_description|More]] about i2Rest Client Flow. |
| − | |||
;OAuth2 Device flow | ;OAuth2 Device flow | ||
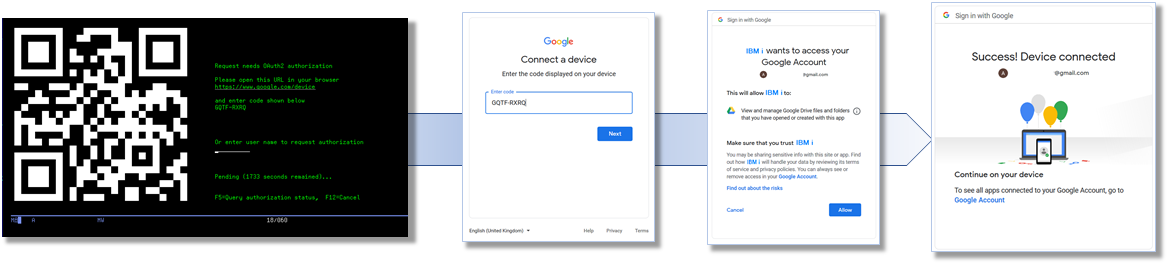
| − | : | + | :Device flow is a flow for those devices (like IBM i) that are not capable to perform a user-agent based authorization. This authorization flow client instructs (by providing an authorization URL) the user to review the authorization request on a secondary device with suitable input and browser capabilities to perform the user interaction. [[Device_flow_description|How]] to use i2Rest Client Device flow, typical use cases - [[i2Rest_Client_Usecases#OAuth2_Device_flow|here]]. |
| − | ;OAuth2 | + | ;OAuth2 Authorization Code flow using i2Rest bridge mode |
| − | : | + | :Authorization Code flow allows an application to obtain an access token (which is a permition to deal with protected user data on remote resource) by exchanging an authorization code for it. In it turn, the authorization code is provided to the application by the authorization server by redirecting the user agent to redirection URI with the authorization code attached. IBM i is not capable of interacting with the resource owner's user-agent (typically a web browser) and is not capable of receiving incoming requests via redirection, so original Authorization Code flow isn't possible using i2Rest Client only. Nevertheless i2Rest Client together with i2Rest Server bridge can do some trick to reproduce this authorization scenario with the same result for the end user. Please look under the hood of [[Authorization_Code_flow_description|Authorization Code flow using i2Rest bridge mode]]. Some use cases are [[I2Rest_Client_Usecases#Oauth2 Authorization code flow with i2Rest bridge|here]]. |
== Implementation == | == Implementation == | ||
| − | <div id="implementation"></div>You can | + | <div id="implementation"></div>You can interact with i2Rest Client [[i2Rest_Client_command|with IBM i command]], or embed calls to [[i2Rest_Client_API|i2Rest Client API]] into your ILE RPG or ILE C programs.<BR/> |
| + | i2Rest Client command and API are installed in a single package along with i2Rest Server - see [[I2Rest_Install|i2Rest installation guide]]. All functions of i2Rest Client are available for free! | ||
Latest revision as of 22:50, 3 September 2020
i2Rest Client is a native IBM i tool for web communications via http/https requests. It was intended to extend IBM i interactive green screen and batch functionality with http client functions. i2Rest Client takes on all the difficulties associated with interaction between your programs and all the outside world - from providing transport functions to implementing various authentication and authorization scenarios (like OAuth2.0 flows), which allows your IBM i to have access to almost any web service.
Request authorization methods
Depending on your target server requirements, you can choose one of the next request authorization metods provided by i2Rest Client:
- Request without authorization
- HTTP/HTTPS requests of any type, JSON messages, stream file upload - everything is here. Please explore typical use cases
- Basic access authentication
- Same options as above, but with Basic access authentication.
The next three methods are the OAuth2.0 flows, which are the way of enabling third party application to have limited access to protected user data on remote resource behalf of a data owner. The benefit of OAuth2.0 flows is that data owners are not forced to share their usernames, passwords, and other private information to third party applictaions.
- OAuth2 Client Credentials flow
- Client Credentials flow should be used to authenticate your IBM i application on remote resource to work with its own data rather than a user's data. More about i2Rest Client Flow.
- OAuth2 Device flow
- Device flow is a flow for those devices (like IBM i) that are not capable to perform a user-agent based authorization. This authorization flow client instructs (by providing an authorization URL) the user to review the authorization request on a secondary device with suitable input and browser capabilities to perform the user interaction. How to use i2Rest Client Device flow, typical use cases - here.
- OAuth2 Authorization Code flow using i2Rest bridge mode
- Authorization Code flow allows an application to obtain an access token (which is a permition to deal with protected user data on remote resource) by exchanging an authorization code for it. In it turn, the authorization code is provided to the application by the authorization server by redirecting the user agent to redirection URI with the authorization code attached. IBM i is not capable of interacting with the resource owner's user-agent (typically a web browser) and is not capable of receiving incoming requests via redirection, so original Authorization Code flow isn't possible using i2Rest Client only. Nevertheless i2Rest Client together with i2Rest Server bridge can do some trick to reproduce this authorization scenario with the same result for the end user. Please look under the hood of Authorization Code flow using i2Rest bridge mode. Some use cases are here.
Implementation
You can interact with i2Rest Client with IBM i command, or embed calls to i2Rest Client API into your ILE RPG or ILE C programs.
i2Rest Client command and API are installed in a single package along with i2Rest Server - see i2Rest installation guide. All functions of i2Rest Client are available for free!