Difference between revisions of "Device flow usecase 1"
Pavel.lobko (talk | contribs) (→Device Flow) |
(→Device flow) |
||
| (60 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | {{DISPLAYTITLE:Google drive API}} | |
| + | The use case shows the process of creating "i2rest.doc" file on "i2restexample" user Google Drive using I2Rest Client request with Oauth2 Authorization code flow. | ||
| + | Lets walk step by step through our example with creating "i2rest.doc" file on "i2restexample" user Google Drive | ||
| − | + | == Preparations == | |
| − | + | :a)At the very beginning your application should be registered as a client (obtaining Device ID and Device Password) on [https://console.developers.google.com/apis/credentials Google] (see [https://developers.google.com/identity/protocols/oauth2 details]). | |
| − | + | :b) [[Create_*SYSTEM_Certificate_Store| Create *SYSTEM Certificate Store]] and [[Add_external_CA_to_trust_list |add Google.com SSL CA ]].<br> | |
| − | At the very | ||
| − | + | == i2Rest Client command composing == | |
| + | Composing i2Rest Client we need:<br> | ||
| + | :to set request method and API endpoint to values that are specified in the API method description; | ||
| + | <pre> | ||
| + | I2REST COMMAND(*POST) | ||
| + | URL('https://www.googleapis.com/drive/v3/files') | ||
| + | </pre> | ||
| + | :to specify properly configured on Preparations step (b) Certificate_Store to be able to work with SSL secured resource; | ||
| + | <pre> | ||
| + | DCMCLIENT(<DCM client name>) | ||
| + | </pre> | ||
| + | :to specify obtained on Preparations step (a) requisites; | ||
| + | <pre> | ||
| + | AUTHID('Device ID') | ||
| + | AUTHPW('Device password) | ||
| + | AUTHURL('https://accounts.google.com/o/oauth2/v2/auth | ||
| + | ') | ||
| + | TOKENURL('https://oauth2.googleapis.com/token') | ||
| + | SCOPE('https://www.googleapis.com/auth/drive.file') | ||
| + | </pre> | ||
| + | All the necessary parameters are specified, it's time to execute the complete command. | ||
| + | <pre> | ||
| + | I2REST COMMAND(*POST) | ||
| + | URL('https://www.googleapis.com/drive/v3/files') | ||
| + | BODY(*N '{"name":"i2rest.doc"}' | ||
| + | 'application/json' *YES 1208) | ||
| + | OUTPUT(*BOTH) | ||
| + | AUTHMETHOD(*OAUTH2D) | ||
| + | DCMCLIENT(MYCLIENT) | ||
| + | RECVLOG('/home/USRX/recieved.log') | ||
| + | SENTLOG('/home/USRX/sent.log') | ||
| + | TOKENS('/tokens/tokens.usrspc') | ||
| + | AUTHID('<Device ID>') | ||
| + | AUTHPW('<Device password>') | ||
| + | AUTHURL('https://oauth2.googleapis.com/device/code') | ||
| + | TOKENURL('https://oauth2.googleapis.com/token') | ||
| + | SCOPE('https://www.googleapis.com/auth/drive.file') | ||
| + | </pre> | ||
| − | + | == Device flow == | |
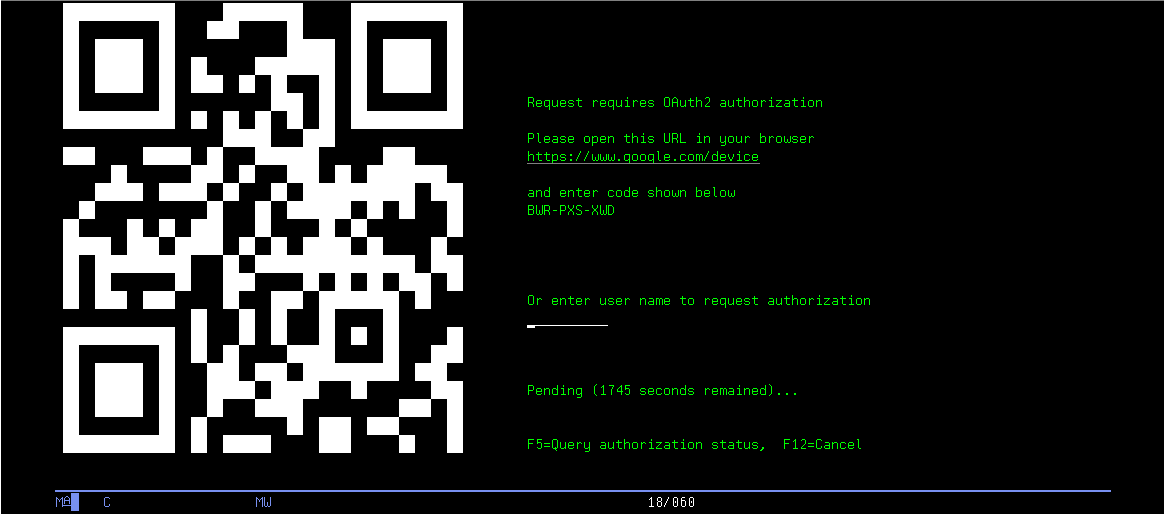
| − | + | After the command was executed, I2Rest Client starts performing Oauth2 Authorization code flow. Steps (A), (B) of the [[Device_flow_description|flow]] are taken behind the scene. Step (C) will be displayed on your green screen. Follow provided link. | |
| − | + | <div style="padding-bottom:6px">[[File:Device-flow-usecase1.png]]</div> | |
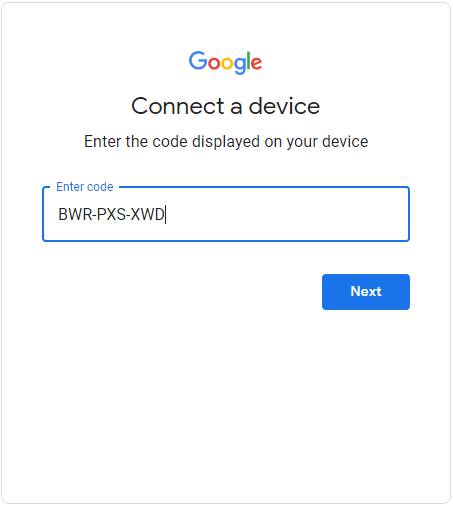
| − | + | Find yourself on device connection page. Proceed with "Next" button, and this is step (D). | |
| − | + | <div style="padding-bottom:6px">[[File:Device-flow-usecase2.png]]</div> | |
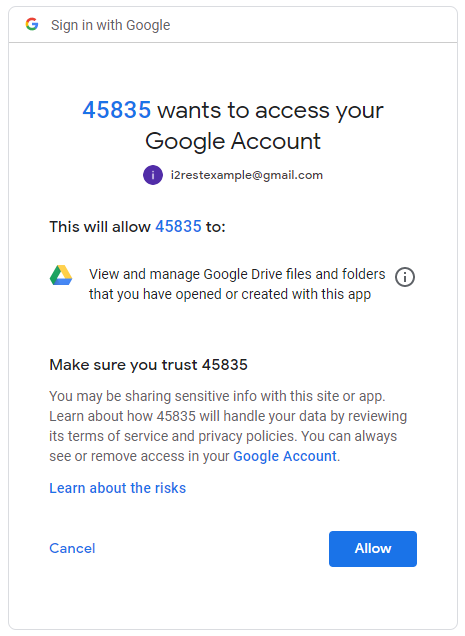
| − | + | Grant access to requested scope. | |
| − | + | <div style="padding-bottom:6px">[[File:Device-flow-usecase3.png]]</div> | |
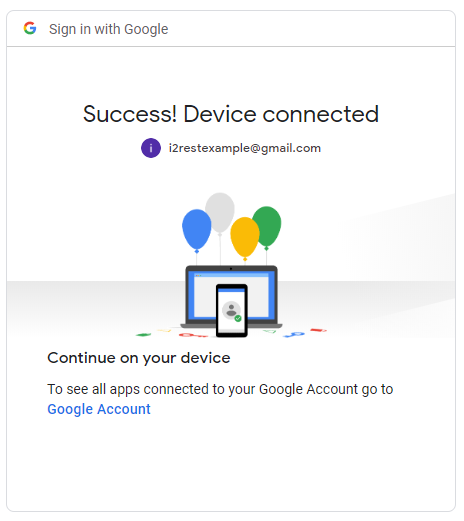
| − | + | Here we are! | |
| − | + | <div style="padding-bottom:6px">[[File:Device-flow-usecase4.png]]</div> | |
| + | Steps (E), (F) of the flow does not envolve end user. | ||
| + | |||
| + | == Checking the result! == | ||
| + | We didn't make a screenshot with i2rest.doc on our example Google Drive, but you can check your own file right now. Also take a look on the result of the authorized request to Google Drive APi in joblog. | ||
| + | <pre> | ||
| + | Approved scopes https://www.googleapis.com/auth/drive.file | ||
| + | Token type Bearer | ||
| + | Token expires in 3599 | ||
| + | Server response (status 200, shown 128 bytes of 128): | ||
| + | { | ||
| + | "kind": "drive#file", | ||
| + | "id": "1qH1yvlK1WF-C8oi9v3Nf8miUTuz_1Tvr", | ||
| + | "name": "i2rest.doc", | ||
| + | "mimeType": "application/msword" | ||
| + | } | ||
| + | </pre> | ||
Latest revision as of 20:38, 2 November 2021
The use case shows the process of creating "i2rest.doc" file on "i2restexample" user Google Drive using I2Rest Client request with Oauth2 Authorization code flow. Lets walk step by step through our example with creating "i2rest.doc" file on "i2restexample" user Google Drive
Preparations
- a)At the very beginning your application should be registered as a client (obtaining Device ID and Device Password) on Google (see details).
- b) Create *SYSTEM Certificate Store and add Google.com SSL CA .
i2Rest Client command composing
Composing i2Rest Client we need:
- to set request method and API endpoint to values that are specified in the API method description;
I2REST COMMAND(*POST)
URL('https://www.googleapis.com/drive/v3/files')
- to specify properly configured on Preparations step (b) Certificate_Store to be able to work with SSL secured resource;
DCMCLIENT(<DCM client name>)
- to specify obtained on Preparations step (a) requisites;
AUTHID('Device ID')
AUTHPW('Device password)
AUTHURL('https://accounts.google.com/o/oauth2/v2/auth
')
TOKENURL('https://oauth2.googleapis.com/token')
SCOPE('https://www.googleapis.com/auth/drive.file')
All the necessary parameters are specified, it's time to execute the complete command.
I2REST COMMAND(*POST)
URL('https://www.googleapis.com/drive/v3/files')
BODY(*N '{"name":"i2rest.doc"}'
'application/json' *YES 1208)
OUTPUT(*BOTH)
AUTHMETHOD(*OAUTH2D)
DCMCLIENT(MYCLIENT)
RECVLOG('/home/USRX/recieved.log')
SENTLOG('/home/USRX/sent.log')
TOKENS('/tokens/tokens.usrspc')
AUTHID('<Device ID>')
AUTHPW('<Device password>')
AUTHURL('https://oauth2.googleapis.com/device/code')
TOKENURL('https://oauth2.googleapis.com/token')
SCOPE('https://www.googleapis.com/auth/drive.file')
Device flow
After the command was executed, I2Rest Client starts performing Oauth2 Authorization code flow. Steps (A), (B) of the flow are taken behind the scene. Step (C) will be displayed on your green screen. Follow provided link.
Find yourself on device connection page. Proceed with "Next" button, and this is step (D).
Grant access to requested scope.
Here we are!
Steps (E), (F) of the flow does not envolve end user.
Checking the result!
We didn't make a screenshot with i2rest.doc on our example Google Drive, but you can check your own file right now. Also take a look on the result of the authorized request to Google Drive APi in joblog.
Approved scopes https://www.googleapis.com/auth/drive.file
Token type Bearer
Token expires in 3599
Server response (status 200, shown 128 bytes of 128):
{
"kind": "drive#file",
"id": "1qH1yvlK1WF-C8oi9v3Nf8miUTuz_1Tvr",
"name": "i2rest.doc",
"mimeType": "application/msword"
}